The Tangled Web of Phishing Schemes: How to Spot the Bait and Secure Your Digital Fortress

Introduction:
As the digital realm expands, so do the tactics of cybercriminals seeking to exploit vulnerabilities. Phishing schemes present a pervasive threat to personal information security by using deceptive tactics to trick individuals into revealing sensitive information, such as login credentials, financial details, or personal information.
These phishing attacks typically involve fraudulent communication, such as emails, text messages, or phone calls, that impersonate trusted entities like banks, social media platforms, or government agencies.
This guide aims to equip individuals with the knowledge and tools necessary to identify, thwart, and report phishing attacks effectively.
Understanding the Peril: Deciphering Phishing Tactics
Before diving into defence strategies, it's essential to understand the modus operandi of phishing attackers. Phishing involves the deceptive acquisition of sensitive information, often through impersonation or manipulation. Cybercriminals employ various tactics, including email spoofing, fake websites, and social engineering, to deceive victims.
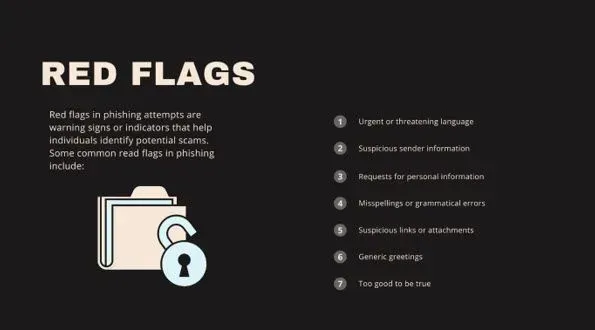
Spotting the Bait: Recognizing Phishing Red Flags
Identifying phishing attempts requires a vigilant mindset and an awareness of common indicators. By recognizing red flags such as unusual requests, suspicious links, poor grammar, and generic greetings, individuals can better protect themselves from falling prey to phishing scams. Let us dive deep into some of the most common vulnerabilities.
Unusual Request: Beware of Unexpected Demands
Phishing emails often include unusual requests, such as urgent pleas for personal information or immediate action.
For instance, receiving an email claiming your account will be suspended unless you provide sensitive data like passwords or credit card numbers is a red flag. Legitimate organizations typically don't ask for such information via email.

Suspicious Links: Exercise Caution Before Clicking
Phishing attacks send emails frequently that contain links that appear legitimate but actually lead to malicious websites. Hovering over the link without clicking can reveal the true destination.
For example, an email seemingly from your bank urging you to update your account information might include a link that, upon closer inspection, directs to a suspicious URL.
Poor Grammar and Spelling: Watch Out for Linguistic Errors
It is imperative to give a keen read to phishing emails because they often contain grammatical and spelling mistakes, indicating a lack of professionalism.
For instance, an email supposedly from a reputable company with obvious errors like "Dear Custoemer" instead of "Dear Customer" raises suspicion. Legitimate organizations typically take care to ensure error-free communication.
Generic Greeting: Look for Personalized Communication
Phishing attackers often use generic greetings like "Dear Customer" instead of addressing recipients by name.
For example, an email claiming to be from your bank that starts with "Dear Valued Customer" instead of addressing you by your name might be suspicious. Legitimate communications usually address recipients by name to establish authenticity.
Real-Life Examples: Unveiling Phishing Tactics
Real-life examples serve as illuminating case studies, revealing the intricate tactics employed by cybercriminals in phishing schemes.
The PayPal Impersonation Scam
In this scheme, cybercriminals impersonate PayPal, a trusted online payment platform, to deceive users into divulging their account credentials. Victims receive emails purportedly from PayPal, alerting them of account issues or unauthorized transactions.
The emails contain links to fake login pages designed to capture users' login credentials, which are then used for fraudulent purposes.
The Banking Credential Harvesting Scheme
In this sophisticated scheme, attackers target banking customers by sending phishing emails disguised as legitimate communication from financial institutions. These emails often claim to contain urgent account alerts or security updates, prompting recipients to click on malicious links or download attachments.
Once clicked, these links lead to fake login pages or malware-infected attachments aimed at harvesting users' banking credentials.
The Corporate Email Compromise Incident
In this type of phishing attack, cybercriminals target businesses by impersonating company executives or trusted vendors. Using carefully crafted emails, attackers deceive employees into initiating unauthorized wire transfers or disclosing sensitive company information.
These attacks exploit trust relationships within organizations, resulting in financial loss and reputational damage.
Empowering Defense: Strategies for Enhanced Cybersecurity
Empowering individuals with robust defense strategies is pivotal in the ongoing battle against cyber threats, fortifying our digital fortresses and ensuring a safer online experience for all. Let us have a look at defensive measures to ensure we can secure ourselves from phishing attacks.
Strengthen Passwords
Utilise complex, unique passwords for each online account to minimize the risk of unauthorized access. Avoid using easily guessable information and consider using a passphrase or password manager for added security.
Enable Two-Factor Authentication (2FA)
Add an extra layer of security to your accounts by enabling two-factor authentication wherever possible. This requires users to provide a secondary verification method, such as a one-time code sent to their mobile device, in addition to their password.
Keep Software Updated
Regularly update your operating system, antivirus software, and applications to patch security vulnerabilities and protect against potential exploits. Enable automatic updates to ensure you're always using the latest, most secure versions.
Educate Employees
Provide comprehensive cybersecurity training to employees to enhance awareness and vigilance against phishing attacks. Educate them on common phishing tactics, red flags to watch out for, and procedures for reporting suspicious emails or incidents.

Conclusion: Safeguarding Your Digital Presence
In conclusion, protecting your personal information from phishing schemes requires a multifaceted approach encompassing awareness, vigilance, and proactive measures. By understanding phishing tactics, recognizing red flags, and implementing robust cybersecurity strategies, individuals can fortify their digital defenses and mitigate the risk of falling victim to malicious attacks.
Remember, in the evolving landscape of cyber threats, staying informed and proactive is key to safeguarding your digital fortress.








