
Introduction
In today's connected digital world, where data has become one of the most valuable assets for organisations, the importance of robust cybersecurity measures cannot be underestimated.
With the rise of potential cyber threats, including ransomware attacks, phishing scams, and insider threats, businesses are increasingly vulnerable to data breaches that can have devastating consequences, ranging from financial losses to reputational damage.
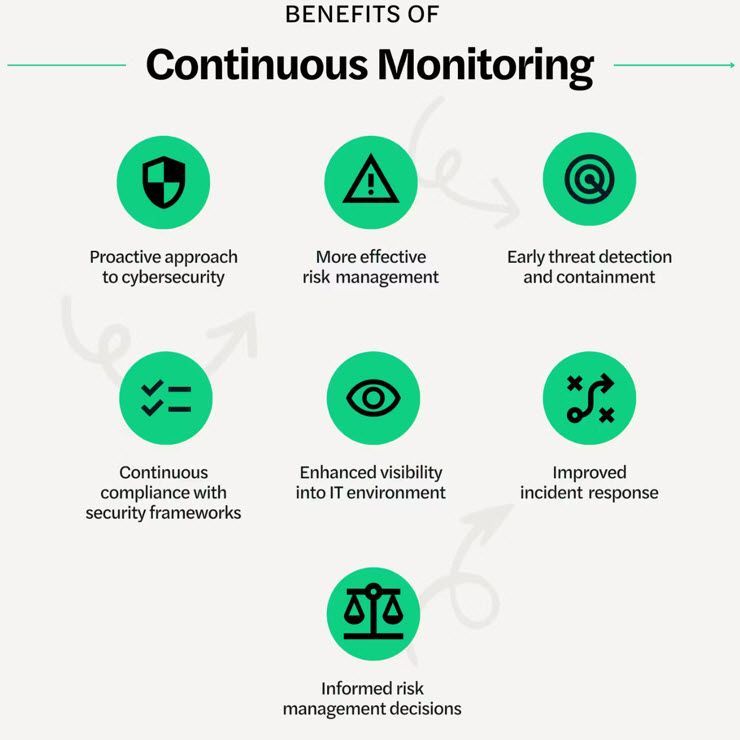
Continuous monitoring protocols in this scenario stand as a crucial pillar in the defence against such cyber threats. Unlike traditional cybersecurity approaches that rely on periodic assessments, continuous monitoring offers a proactive and real-time approach to detecting and responding to security incidents.
Importance of Continuous Monitoring in Cybersecurity
Real-Time Threat Detection
Continuous monitoring enables organisations to detect security threats in real-time, allowing you to prompt responses to potential breaches before they escalate.
Proactive Risk Management
By continuously monitoring network activity, system logs, and user behaviour, organisations can proactively identify and address security vulnerabilities.
Minimisation of Dwell Time
Continuous monitoring helps minimise the dwell time of attackers within the network by promptly detecting and mitigating security incidents.
Enhanced Incident Response
With real-time visibility into security events and incidents, organisations can develop more effective incident responses.
Adaptation to Evolving Threats
Continuous monitoring allows you to stay ahead of emerging cyber threats and adapt their security defences accordingly.
Understanding Real-Time Detection Mechanisms
Real-time detection mechanisms serve as the frontline defence against cyber threats, providing you with the means to identify and mitigate potential breaches before they inflict substantial damage.
Intrusion Detection Systems (IDS)
Intrusion Detection Systems (IDS) are critical components of real-time threat detection. They can monitor network traffic and identify suspicious or malicious activities that may indicate unauthorised access attempts or cyberattacks.
IDS can be classified into two main categories: network-based IDS (NIDS) and host-based IDS (HIDS).
Network-Based IDS (NIDS)
NIDS sensors analyse network traffic in real-time, using predefined signatures or behavioural analysis techniques to detect anomalies or signs of malicious activity. Network-based IDS can identify potential threats such as port scans, denial-of-service (DoS) attacks, and malware infections by monitoring network packets and traffic patterns.
Host-Based IDS (HIDS)
Host-based IDS solutions operate at the individual host level, monitoring system logs, file integrity, and application activity for signs of unauthorised access or suspicious behaviour. They can detect activities such as unauthorised file modifications and privilege escalation attempts.
Security Information and Event Management (SIEM) Platforms
Security Information and Event Management, aka SIEM platforms, play a crucial role in real-time threat detection by aggregating, correlating, and analysing security.
SIEM platforms collect data from network devices, servers, applications, and security tools, providing centralised visibility into security incidents and anomalies. It works in the following manner.

Log Aggregation and Correlation
SIEM platforms collect and aggregate logs and security events from disparate sources, then correlate related events to identify potential security incidents or patterns of malicious activity.
Timely Alerting and Notification
Once logs are aggregated and correlated, they generate alerts and notifications in real time based on predefined correlation rules, thresholds, and anomaly detection algorithms.
Forensic Analysis and Incident Response:
Finally, SIEM progresses with forensic analysis and incident response by providing comprehensive visibility into security events, enabling security teams to reconstruct timelines, analyse attack vectors, and mitigate security breaches effectively.
Endpoint Detection and Response (EDR) Solutions
Endpoint Detection and Response, also known as EDR solutions, focus on real-time monitoring and response capabilities at the endpoint level, providing you with granular visibility into endpoint activities and behaviours.
Endpoint Detection and Response leverage endpoint agents to monitor system activities, detect suspicious behaviour, and respond to security incidents in real-time.
Behavioural Analysis and Machine Learning
These solutions employ behavioural analysis and machine learning algorithms to identify abnormal or malicious behaviour on endpoints, such as malware execution or credential theft.
Potential Threat Hunting and Investigation
They also enable proactive threat hunting and investigation by providing security teams with the tools and capabilities to query endpoint data. Then, they conduct forensic analysis and identify indicators.
Automated Response and Remediation
EDR solutions support automated response and remediation actions. This automated response allows organisations to quarantine or isolate compromised endpoints and terminate malicious processes in real-time.

Key Takeaway
Continuous monitoring protocols are indispensable in today's cybersecurity framework. They allow you to detect and respond to data breaches in real-time. You can significantly enhance cybersecurity defences and safeguard sensitive data against evolving threats by leveraging automation, machine learning, and robust incident response procedures.
Implementing Continuous Monitoring Protocols in Real-Time
Implementing continuous monitoring protocols is essential to strengthen your cybersecurity defences and minimise the risks of data breaches and cyberattacks.
Assessing Your Needs and Risks
Calculated Risk Assessment
First, you must conduct a comprehensive risk assessment to identify potential security threats and vulnerabilities.
Asset Inventory
Then, you must develop an inventory of critical assets, including networks, systems, applications, and data repositories.
Utilise Threat Modeling
Finally, you should utilise threat modelling techniques to identify potential attack vectors and scenarios, allowing you to tailor your monitoring.
Selecting Appropriate Tools and Technologies
Upto Date Technology Evaluation
Choose continuous monitoring tools and technologies that align with your requirements, budget, and technical capabilities. It includes multiple factors such as scalability, interoperability, and ease of deployment.
Integration Capabilities with Existing Infrastructure
Ensure seamless integration of continuous monitoring solutions with existing security infrastructure, including network security appliances and endpoint protection platforms.
Automation and Orchestration
To autonomously detect breaches in real-time, you should leverage automation and orchestration capabilities to automate routine tasks and improve efficiency in threat detection and response processes.
Integrating Continuous Monitoring into Existing Cybersecurity Frameworks
Framework Alignment with Standards
Align continuous monitoring protocols with established cybersecurity frameworks and standards, such as the NIS and Cybersecurity Framework, to ensure adherence to best practices.
Customised Policy Development
Develop policies that govern continuous monitoring activities, including data collection and retention, incident response protocols, and escalation procedures.
Mandatory Training and Awareness
It is essential to provide ongoing training and awareness programs to educate employees about the importance of continuous monitoring and best practices for identifying and reporting security incidents.
Conclusion
In conclusion, continuous monitoring protocols are essential to a comprehensive cybersecurity strategy.
Adopting and integrating these protocols into existing frameworks can enhance their ability to detect and respond to data breaches effectively.
With the ever-increasing potential of cyber threats, continuous monitoring is a critical defence mechanism, enabling businesses to stay ahead of malicious actors and safeguard their valuable assets.
Be informed. Stay updated.
Stay ahead with the
HermesHerald newsletter!
Immerse yourself in exclusive insights and crucial updates. Ensure you're always in the know!
Contact Us
Thank you for signing up to HermesHerald! We're excited to keep you updated with the latest insights and information. Stay tuned! 🌟
Please try again later.
Contact Us
Thank you for signing up to HermesHerald! We're excited to keep you updated with the latest insights and information. Stay tuned! 🌟
Please try again later.
Contact Us
Thank you for signing up to HermesHerald! We're excited to keep you updated with the latest insights and information. Stay tuned! 🌟
Please try again later.
With over 40 years combined experience, we conduct professional investigation and intelligence services for local and international clients in the public, private, and law enforcement sectors.
Website Privacy Policy & GDPR | Operational Policy
BROWSE WEBSITE
CONTACT INFO
Phone:
1800 889 713
Email: help@cyberlutions.com.au
Location:
Suite 88, 30 Denison St, Bondi Junction NSW 2022
Location:
Unit 4, 95 Main Rd, George Town TAS 7253
BUSINESS HOURS
- Mon - Fri
- -
- Sat - Sun
- Closed
With over 40 years combined experience, we conduct professional investigation and intelligence services for local and international clients in the public, private, and law enforcement sectors.
BROWSE WEBSITE
CONTACT INFO
Phone: 1800 889 713
Email: help@cyberlutions.com.au
Location: Suite 88, 30 Denison St, Bondi Junction NSW 2022
Location: Unit 4, 95 Main Rd, George Town TAS 7253
BUSINESS HOURS
- Mon - Fri
- -
- Sat - Sun
- Closed
Copyright CYBERLUTIONS, All Rights Reserved
Content, including images, displayed on this website is protected by copyright laws. Downloading, republication, retransmission or reproduction of content on this website is strictly prohibited. Website Privacy Policy & GDPR | Operational Policy | Cookie Policy








