Securing Communication Channels from Eavesdropping using End-to-End Encryption

What is End-to-End Encryption?
End-to-end encryption is like having a secret code for your messages.
It means that only you and your intended recipient will be able read what you send. Even if someone tries to intercept, they won't be able to understand your messages, since they are encrypted.
For example, sending a letter in a locked box. Only you and your recipient have the keys to unlock the box and read the letter. That's how end-to-end encryption works for digital messages.
There are different types of encryption, but end-to-end encryption is special because it keeps your messages safe all the time.
End-to-end encryption keeps your messages safe from start to finish. While using other encryption schemes, your data may be safe while traveling but may become vulnerable when they're stored on that server.
Why Privacy is Critical in Communication?
Privacy in communication is crucial, as it protects personal information and sensitive data from falling into the wrong hands.
Risks of Unauthorised Access
Whether it's cybercriminals, government surveillance, or data breaches, the consequences of privacy breaches can be severe.
By prioritising privacy in the communication channels, it mitigates the risk of sensitive information being compromised.
Protecting Sensitive Information
Whether engaging in personal or business communications, safeguarding sensitive information is essential.
End-to-end encryption ensures that all the messages remain confidential. It also makes them inaccessible to anyone other than the intended recipient.
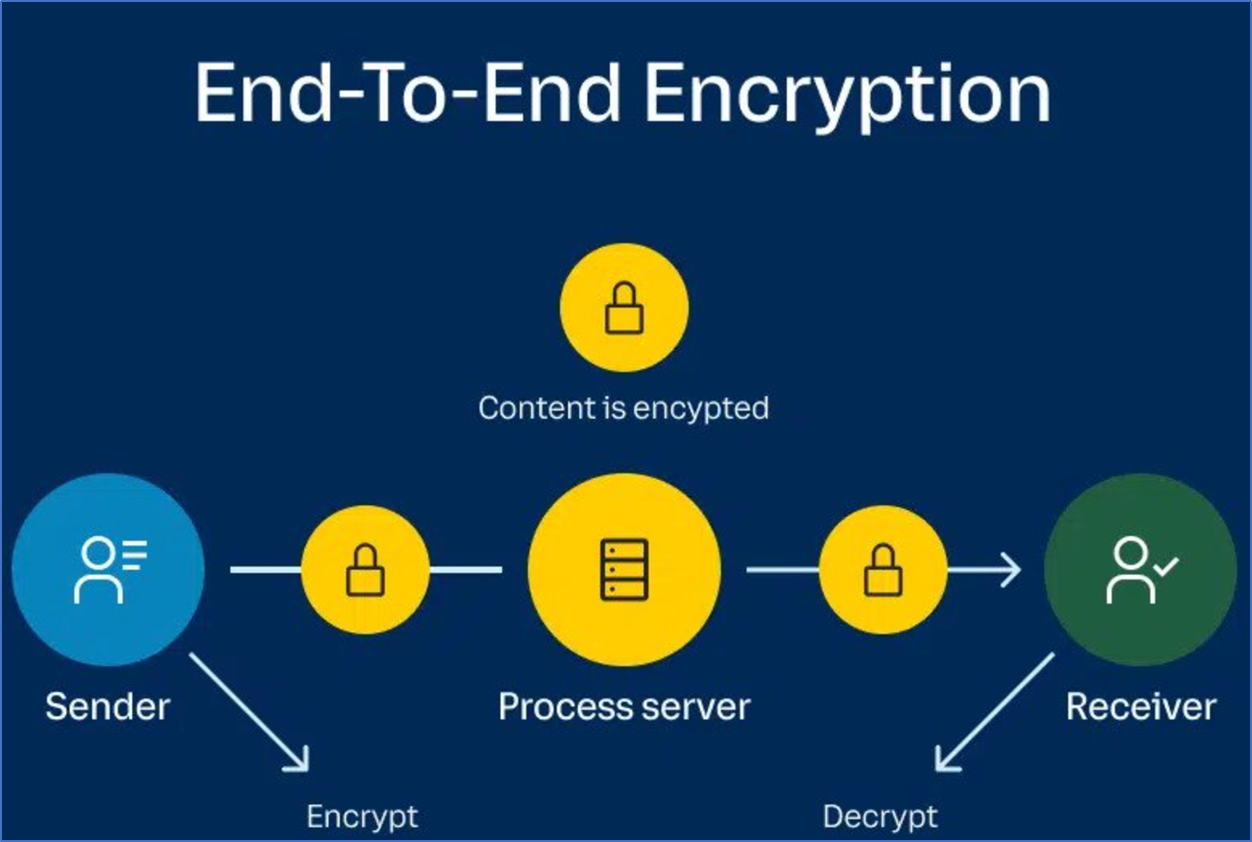
How End-to-End Encryption Works
Let's dive deeper into how end-to-end encryption. It keeps your messages safe by turning them into secret codes that only you and your recipient can understand.
Step Wise Process of Encryption and Decryption
Encryption is like turning your message into a secret code before sending it.
This code is made using complex algorithms. Resembling math puzzles, it scrambles your message into something unreadable.
At the sender's end, your message gets transformed into this secret code using a special key.
This key is like the key to a locked box, and only you and your recipient have it.
When the coded message reaches your recipient, they use their key to unlock the box and decode the message back into its original form.
This process ensures that only you and your recipient can read the message, keeping it safe from anyone trying to sneak a peek in between.

Key Generation and Management
In encryption, the keys are like the secret ingredients that make end-to-end encryption work. There are two types of keys 'public keys' and 'private keys'.
Public keys are like locks that anyone can use to send you encrypted messages. You share your public key with others so they can use it to lock their messages before sending them to you.
Private keys are like the special keys that only you have to unlock the messages encrypted with your public key. You keep your private key safe and secure because if someone else gets hold of it, they could read your encrypted messages.
Key generation and management are crucial to ensuring the security of end-to-end encryption. It's important to use strong, unique keys and to keep your private key safe from unauthorised access.
Applications of End-to-End Encryption
Let me guide you through where you can find end-to-end encryption in action and how you can implement it to safeguard your digital communications across various platforms.
Messaging Apps
Applications like Threema, Status, WhatsApp, Signal, Session and Telegram (just to name a few) prioritise your privacy by employing robust end-to-end encryption protocols.
With end-to-end encryption in place, every message you send is transformed into a secret code before it leaves your device.
This code can only be deciphered by the intended recipient, ensuring the privacy of your conversation.
You can trust that your communications are for texting, sharing photos, and voice notes.
Email Services
For secure email communications, ProtonMail and Tutanota are prioritised as these platforms offer end-to-end encryption to protect your emails from interception.
With end-to-end encryption enabled, your emails are encrypted on your device before they're sent, and only the recipient with the decryption key can access the contents.
Cloud Storage Solutions
When storing your files and documents in the cloud, always choose end-to-end encryption platforms. Popular services like pCloud, tresorit, Dropbox and iCloud (just to name a few) provide encryption to enhance the security of your stored files.
With end-to-end encryption enabled, your files are encrypted both during transmission and while at rest on the cloud servers.
It means that even if someone gains access to the server, they won't be able to access your files without the encryption key.
Key Takeaway
End-to-end encryption is the gold standard for protecting your digital conversations from unauthorised access. Using this technology, you ensure that only you and your intended recipient can decrypt and read your messages, keeping sensitive information safe from prying eyes.
Conclusion
End-to-end encryption stands as a formidable defense against the threats of cyber threats, data breaches, and intrusive surveillance.
By incorporating this technology, you can enjoy greater confidence in the privacy and security of your online communications.
From messaging apps to email services and cloud storage solutions, the adoption of end-to-end encryption is a proactive step towards safeguarding sensitive information in today's digital landscape.









