
The tech-driven world is constantly under siege by cyberattacks, and businesses of all sizes are on the front lines. Identifying new threats and understanding the specific risks to their industry is a challenge.
That's where threat intelligence steps in, giving access to the latest cyber threats, understanding attacker motives and methods, all before they can strike. In this guide, you’ll discover what exactly it is and how to use it to mitigate online risks.
Let’s get into it.

What is Threat Intelligence?
Threat intelligence is like having a team of expert detectives always on the lookout for cyber threats. It provides insider knowledge on evolving attack methods from the dark web and hacker forums. The best part of it is that it's automated, which is why it’s wildly used by businesses and security teams.
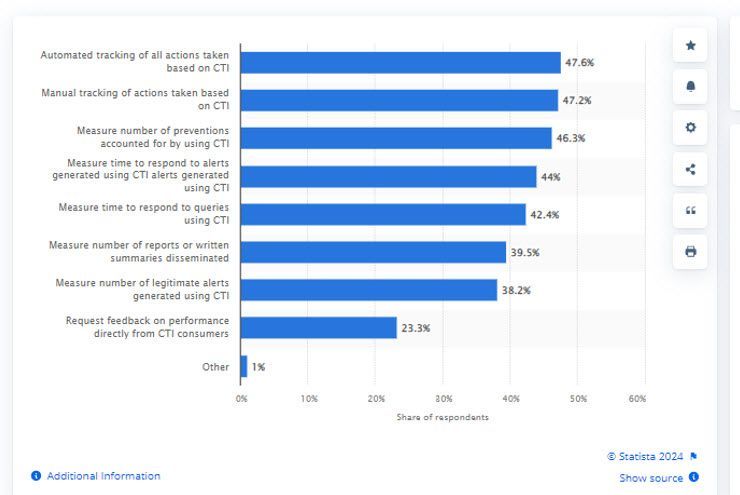
With threat intelligence, you don’t just get a list of bad websites or suspicious IPs. You get context: who is likely to attack you, what techniques they might use, and what your specific weaknesses are.
There are three main types of it:
- Strategic: It helps you understand the overall risk landscape, how your industry is targeted, and where to make long-term security investments.
- Tactical: These are the technical details you need for immediate action – lists of malicious websites, malware signatures, and other indicators that an attack might be underway.
- Operational: It helps you identify who is behind attacks, what their goals are, and how they operate, allowing for better incident response.
Businesses commonly use software tools to aggregate, filter, and analyse open-source threat data.
Plus, vendors can also provide software platforms, expert teams, or dashboards for accessing curated threat feeds, analysis, and alerts tailored to your business.
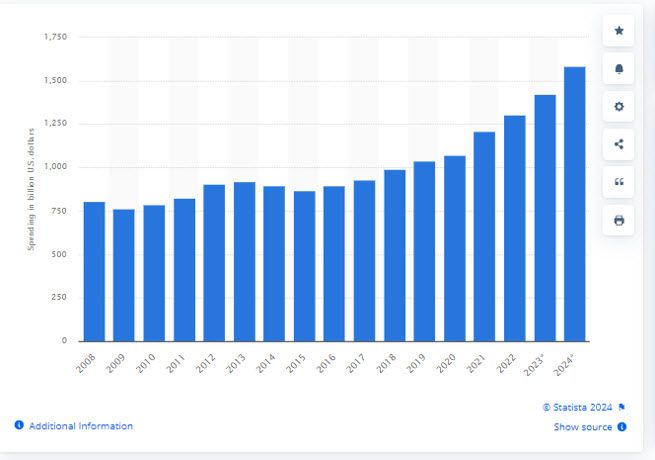
Worldwide spending on Information Technology (IT) services experienced significant growth from 2008 to 2024, according to a report by
Statistica (image below). That growth trend underscores the increasing reliance of businesses and organisations on IT services to drive efficiency, innovation, and competitiveness.
Strategies to Use Threat Intelligence for Risk Mitigation
Here are four key strategies to leverage threat intelligence for robust risk mitigation:
Anticipate Attacks Before They Strike
Start by subscribing to threat feeds relevant to your industry and the types of attacks (ransomware, phishing, etc.) that worry you most. Analyse threat reports. Focus on insights related to your business, like related to the software you use or the regions you operate in.
Patch vulnerable systems, adjust firewall rules, and warn employees about potential risks and what to look for.
Focus on Your Unique Vulnerabilities
Conduct a thorough analysis of your own technology infrastructure, including software, cloud services, and network layout. Combine this self-awareness with threat intelligence focused on your industry to identify your most concerning vulnerabilities.
Target the weaknesses that pose the greatest risk based on the threats you will likely face. If credential theft is a worry, implement multi-factor authentication.
Also, consider investing in specialised threat detection tools for critical vulnerabilities.
Minimise Damage from Breaches
Integrate threat intelligence feeds into your monitoring systems, such as firewalls, antivirus software, and Security Information and Event Management (SIEM) solutions. That enables real-time analysis of potential threats.
Next, prioritise automated alerts based on severity and their resemblance to the threats identified in your intelligence feeds.
And to ensure readiness, have clear, step-by-step incident response plans ready for urgent alerts. These playbooks should outline actions like isolating infected systems, blocking malicious communications, and resetting compromised credentials.
Invest in Security Where it Matters Most
Track the evolution of threats your organisation faces over time, ensuring threat intelligence analysis isn't a one-time activity. Correlate this data with your security spending. Are investments counteracting the actual risks you've documented?
Consider the documented threat reports when choosing new tools, deciding on patching priorities, or planning employee training. That helps maximise the return on your security investments.

Tips for Implementing Threat Intelligence
Turning threat intelligence into a robust defence system requires careful planning. Here are some key factors to consider when implementing threat intelligence solutions:
Build Team According to Your Needs
The choice between building an in-house threat intelligence team or partnering with an external provider depends on your organisation's size, resources, and specific needs.
Creating an internal team gives you more control but needs investment in people and tools.
For small and medium-sized businesses, partnering with a trusted threat intelligence provider is often a smart move. It gives you curated feeds, expert analysis, and advanced threat detection without needing a dedicated team.
Build Automation
To get the most out of threat intelligence, integrate it directly into your firewalls, intrusion detection systems, and SIEM solutions. Real-time integration allows for automated detection and prioritisation of potential threats.
That helps your security team stay focused on the most urgent issues and enables far faster response times to emerging attacks.
Don't Panic in the Attacks
Don't wait until an attack hits to figure out your response. Have predetermined action plans in place for different threat severity levels.
Your plans should outline clear steps for isolation, containment, threat analysis, and communication with both internal stakeholders and, potentially law enforcement. That proactive planning streamlines response, minimises chaos, and protects your organisation by ensuring swift action when it matters most.
Harness the Power of Threat Intelligence: Partner with Cyberlutions®
All in all, threat intelligence is critical for businesses looking to mitigate online risks and protect their valuable assets. It gives you a major advantage by letting you see attacks coming and prepare in advance. You'll know exactly where to strengthen your defenses, and best of all, threat intelligence will help you spend your security budget wisely, protecting what matters most.
However, one thing is clear: the threat landscape is always changing, and securing your business requires proactive strategies. At Cyberlutions®, we don't just provide threat information; we turn it into actionable solutions. Our experts offer tailored threat intelligence, industry insights, and proven strategies to help you beat cybercriminals.
Reach out for a personalised consultation. Let's build a strong, secure future for your business together.
References:
- https://www.linkedin.com/pulse/cyber-threat-intelligence-identifying-mitigating-8strc
- https://www.isaca.org/resources/isaca-journal/issues/2023volume-5/leveraging-threat-intelligence-to-proactively-mitigate-emerging-cybervulnerabilities
- https://www.darkreading.com/threat-intelligence/mitigating-risk-with-threat-intelligence
- https://www.isaca.org/resources/news-and-trends/industry-news/2022/how-to-use-cyberthreat-intelligence-to-proactively-reduce-cyberrisk
- https://socradar.io/how-to-use-threat-intelligence-for-fraud-detection-and-prevention/
Be informed. Stay updated.
Stay ahead with the
HermesHerald newsletter!
Immerse yourself in exclusive insights and crucial updates. Ensure you're always in the know!
Contact Us
Thank you for signing up to HermesHerald! We're excited to keep you updated with the latest insights and information. Stay tuned! 🌟
Please try again later.
Contact Us
Thank you for signing up to HermesHerald! We're excited to keep you updated with the latest insights and information. Stay tuned! 🌟
Please try again later.
Contact Us
Thank you for signing up to HermesHerald! We're excited to keep you updated with the latest insights and information. Stay tuned! 🌟
Please try again later.
With over 40 years combined experience, we conduct professional investigation and intelligence services for local and international clients in the public, private, and law enforcement sectors.
Website Privacy Policy & GDPR | Operational Policy
BROWSE WEBSITE
CONTACT INFO
Phone:
1800 889 713
Email: help@cyberlutions.com.au
Location:
Suite 88, 30 Denison St, Bondi Junction NSW 2022
Location:
Unit 4, 95 Main Rd, George Town TAS 7253
BUSINESS HOURS
- Mon - Fri
- -
- Sat - Sun
- Closed
With over 40 years combined experience, we conduct professional investigation and intelligence services for local and international clients in the public, private, and law enforcement sectors.
BROWSE WEBSITE
CONTACT INFO
Phone: 1800 889 713
Email: help@cyberlutions.com.au
Location: Suite 88, 30 Denison St, Bondi Junction NSW 2022
Location: Unit 4, 95 Main Rd, George Town TAS 7253
BUSINESS HOURS
- Mon - Fri
- -
- Sat - Sun
- Closed
Copyright CYBERLUTIONS, All Rights Reserved
Content, including images, displayed on this website is protected by copyright laws. Downloading, republication, retransmission or reproduction of content on this website is strictly prohibited. Website Privacy Policy & GDPR | Operational Policy | Cookie Policy








