
Introduction
In our modern digital world, where technology plays a central role in our daily lives, the security of our data has become more critical than ever before. However, despite our best efforts, data breaches are inevitable to occur, keeping our privacy at stake.
What is Incident Response Planning and Why is it Critical?
When a data breach happens, how a company responds can make a huge difference. It is where incident response comes into play.
Incident response is like a well-thought-out playbook that guides organisations on what to do when a data breach occurs. It's a series of steps and actions taken to manage and minimise the impact of the breach.
Incident Response Planning is a pre-emptive approach in case of a data breach. It gives you insight into what to do in case of a data breach. It helps you in the identification and resolution of cybersecurity incidents. Moreover, it also helps you minimise downtime & financial losses.
Having a solid incident response plan in place can help you control your nerves in case of a data breach. It helps you respond quickly and effectively, mitigating the breach damage while ensuring privacy.
Basic Elements of Incident Response Planning
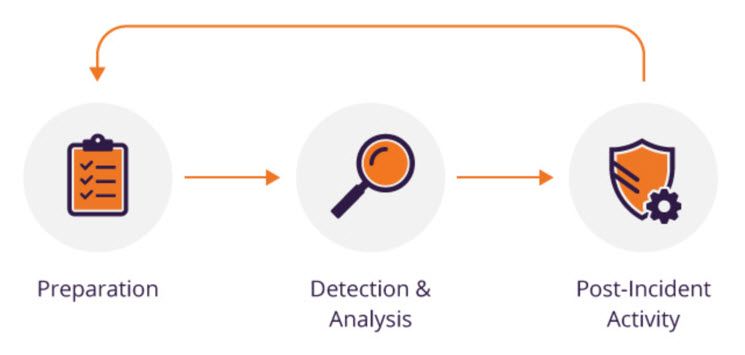
Incident Response Planning is a complex task and it has different phases. The below phases lead to making up a solid plan.
The Preparation Phase
The first step, called the preparation phase, includes risk assessment, creating an incident response team, and developing policies. Let us explore these steps in detail.
Assess the Potential Risk
The risk assessment involves identifying potential threats to your data. It also involves evaluating the impact of those threats. It is basically identifying the weak spots in your network so you can reinforce them.
Build Efficient Incident Response Team
You must develop a team of responsible individuals who will take prompt action in case of any breach. It should be a versatile team consisting of individuals from all concerned departments.
Develop Compliance Policies and Procedures
Your incident response plan needs clear policies and procedures for responding to incidents. These should convey roles and responsibilities and escalation procedures.
The Detection and Analysis Phase
Now that we've got our team ready and our policies in place, let's talk about how we spot trouble and figure out what's going on when something suspicious happens.
Implementation of Monitoring and Detection Systems
You need solid monitoring and detection systems to spot threats in time. These systems must continuously monitor network traffic, logs, and other data sources for any signs of suspicious activity.

Identification and Verification of Incidents
When a potential security incident is detected, it's essential to investigate and verify it immediately. That involves gathering evidence and analysing the scope and impact of the incident. You have to verify whether it was a genuine threat or just a false alarm.
Containment, Elimination, and Recovery Phase
Isolate the Affected Systems or Networks
Once a security breach is confirmed, the next step is to contain it to prevent further damage. It involves separating the affected systems from the normal ones to stop the spread of malware.
Removing Threats and Restoring Systems
With the threat contained, its time to remove the threats and bring the system back in its working state. That involves removing malware, patching vulnerabilities, and restoring data from backups.
Key Takeaway
Incident response planning is crucial in today's digital world to mitigate the impact of data breaches. By understanding its components and implementing best practices, you can effectively detect and recover from security incidents.
Post-Incident Activity
Conducting a Post-Mortem Analysis:
It is crucial to find out the root cause of the incident. Once the incident has been resolved, a thorough post-mortem of the incident is required. It includes reviewing incident response actions, identifying areas for improvement, and updating the incident response plan accordingly.
Updating and Improving Incident Response Plan
Finally, it would help if you improve your incident response plan while learning the lessons from recent incidents. It involves refining the current procedures, updating contact lists, and implementing additional security controls.
Best Practices for Incident Response Planning
We've covered the basics of incident response planning; let's talk about some best practices to help you build a solid plan that'll keep your data.
Train and educate your team
Your incident response team needs to be well-trained and ready to spring into action at any given moment. It requires regular training sessions and simulations to keep their skills sharp and accordingly, will defend your system.
Regular Testing and Drills
Regular drills help you identify any weaknesses or gaps in your plan. It also gives your team valuable hands-on experience in responding to simulated security incidents.
Collaboration and Communication:
Make sure your incident response team knows how to reach out to each other quickly and easily during an episode or incident. Holding your nerves in case of an incident would prevent major loss.
Document Everything
It is very important to investigate the recent incident. It would help if you documented what actions were taken, who was involved, and what lessons were learned. It won't only help you learn from your mistakes but also provide valuable evidence in case of legal or regulatory inquiries.
Update and Adapt to Late Practices
Cyber threats are constantly evolving, so your incident response plan needs to evolve, too. It means revising the current procedures, updating contact lists, and investing in new technologies that will bolster your defenses.
Conclusion
In conclusion, incident response planning is imperative for the secure growth of your business. You need to acknowledge the inevitability of cyber threats and prepare accordingly.
By following a structured incident response plan, you can minimise the impact of data breaches and protect your assets.
Continuous improvement and adaptation to evolving threats are key to staying ahead in the cybersecurity landscape. Remember, it's not a matter of if but when a breach will occur, so be prepared.
Be informed. Stay updated.
Stay ahead with the
HermesHerald newsletter!
Immerse yourself in exclusive insights and crucial updates. Ensure you're always in the know!
Contact Us
Thank you for signing up to HermesHerald! We're excited to keep you updated with the latest insights and information. Stay tuned! 🌟
Please try again later.
Contact Us
Thank you for signing up to HermesHerald! We're excited to keep you updated with the latest insights and information. Stay tuned! 🌟
Please try again later.
Contact Us
Thank you for signing up to HermesHerald! We're excited to keep you updated with the latest insights and information. Stay tuned! 🌟
Please try again later.
With over 40 years combined experience, we conduct professional investigation and intelligence services for local and international clients in the public, private, and law enforcement sectors.
Website Privacy Policy & GDPR | Operational Policy
BROWSE WEBSITE
CONTACT INFO
Phone:
1800 889 713
Email: help@cyberlutions.com.au
Location:
Suite 88, 30 Denison St, Bondi Junction NSW 2022
Location:
Unit 4, 95 Main Rd, George Town TAS 7253
BUSINESS HOURS
- Mon - Fri
- -
- Sat - Sun
- Closed
With over 40 years combined experience, we conduct professional investigation and intelligence services for local and international clients in the public, private, and law enforcement sectors.
BROWSE WEBSITE
CONTACT INFO
Phone: 1800 889 713
Email: help@cyberlutions.com.au
Location: Suite 88, 30 Denison St, Bondi Junction NSW 2022
Location: Unit 4, 95 Main Rd, George Town TAS 7253
BUSINESS HOURS
- Mon - Fri
- -
- Sat - Sun
- Closed
Copyright CYBERLUTIONS, All Rights Reserved
Content, including images, displayed on this website is protected by copyright laws. Downloading, republication, retransmission or reproduction of content on this website is strictly prohibited. Website Privacy Policy & GDPR | Operational Policy | Cookie Policy








